Twitter is, by default, a public platform. When we tweet, we generally don't visualise every possible person who might be reading the tweet or looking at our photos - now, or in five years, ten years into the future.
We might not want to give out so much information about who we are, what we do, who we're friends with and where we are or are likely to be.
How to change your default settings
If you use Twitter in your browser
In your browser: Click on your profile picture --> settings --> security and privacy → and check the following boxes:
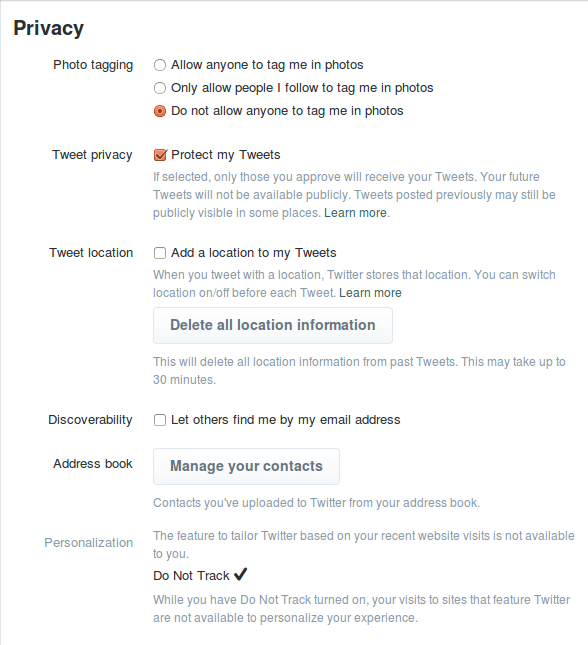 Photo Tagging --> Check: Do not allow anyone to tag me in photos
Photo Tagging --> Check: Do not allow anyone to tag me in photos
Though others can still upload photos of you, you now can't be publicly tagged in them.
Tweet Privacy --> Check: Protect My Tweets
People will now need your permission before they can follow you (though you will keep all the followers you have now). Future tweets will only be visible to your followers, no-on can retweet your tweets, and your tweets will not show up in Google search results.
Limitations: you can't reply to tweets posted by non-followers.
Note: this only works on future tweets; all past tweets will still be public.
Tweet location → Uncheck: Add a location to my tweets
Unchecking this box prevents you accidentally posting a tweet which includes your location.
If the box is checked: With each tweet you send you have the option to add location data or not.
Note: Location data can tell a very detailed story about you, and there are online tools available that enable people to easily map your movements.
Discoverability --> Uncheck: Let others find me by my email address
People now can't find your Twitter account by searching your email address. This is especially important if you have a pseudonymous Twitter account, or if you do not want your email address publicly linked to your account.
If you use Twitter on your mobile
Click on Me --> ![]() --> your account ('OnonymousTTC', for example) --> privacy
--> your account ('OnonymousTTC', for example) --> privacy
Photo Tagging --> Turn it off
Though others can still upload photos of you, you can't be publicly tagged in them.
Tweet Privacy --> Turn it on
People will now need your permission before they can follow you (though you will keep all the followers you have now). Future tweets will only be visible to your followers, no-on can retweet your tweets, and your tweets will not show up in Google search results.
Limitations: you can't reply to tweets posted by non-followers.
Note: this only works on future tweets; all past tweets will still be public.
Discoverability --> Turn it off
People now won't be able to find your Twitter account by searching your email address. This is especially important if you have a pseudonymous Twitter account, or if you do not want your email address publicly linked to your account.
If you want to create an "anonymous" Twitter account
To increase your privacy you can use a pseudonym and a random picture, but when you register for a Twitter account, your email address and mobile phone number are asked for.
If you register for your account through your browser (not your phone), you can avoid giving your mobile phone number, but you still have to provide a an email address. For more on how to set up an alternative email account, go here.
To create an 'anonymous' account → go to your browser → register with a pseudonym and an anonymous email account → skip the steps that require personal data.
Note: If creating a Twitter account with a pseudonym, be careful not to use the same email address, phone number or profile picture as your other online accounts (unless these are all linked to the same pseudonymous identity). This will increase the likelihood that other people can tie your pseudonymous Twitter account to your other accounts.
Note: pseudonymity on a commercial platform is always only skin-deep. Unless you take other precautions, Twitter has access to the email address and/or phone number you provide when registering for an account, as well as your IP address when you use Twitter to send a Tweet, and possible data from cookies in your browser.
Tips to increase your privacy on Twitter
Linking twitter to other accounts
Limit third party linking to your Twitter account. Some websites, social networks and apps give you the option to sign in or to verify your identity by linking your Twitter account to their service.
Note: If you do this, you're giving the third party (the website, social network or app) access to your Twitter username, your lists of followers and following, your location (if you share it) and your tweets - even if you've set them to "Private". You will also be giving Twitter information about the other services that you use.
How private are your direct messages?
Direct messages are private messages you can send to other tweeters. Note that other Twitter users will not see these messages, but Twitter always has access to them and can store messages even when you have deleted them.
Delete all location information from past Tweets.
Twitter gives you the option to add location to your tweets. You can delete your location information from past Tweets:
Go to your profile picture --> settings --> security and privacy → Tweet location → and press 'Delete all location data'
Note: This deletes the public location data from your past tweets, but Twitter can still store this information.
How to create private Twitter lists
When you follow many accounts, Twitter can become overwhelming. Twitter lists are a way to filter the things you are interested in.
How does this work? Say you create a list called 'Environment' for tweets related to the environment. You add people who tend to tweet about environmental issues. Now you have a choice to make your list either public or private.
Public list: Can be seen by your followers. The people you have added to the list will be notified by email.
Private list: This list is for your eyes only, and will not be visible to either your followers or the people included in the list. Note, however, that Twitter also has access to it.
Security: Login Verification
Twitter offers you a security feature to confirm your login with phone verification. This can be found under Security & Privacy -> Login verification. This will help protect your account if someone else has managed to get hold of your password.
The "cost" of this security feature is that you need to give your phone number to Twitter.
